IoT Security - A Damn Vulnerable Intercom
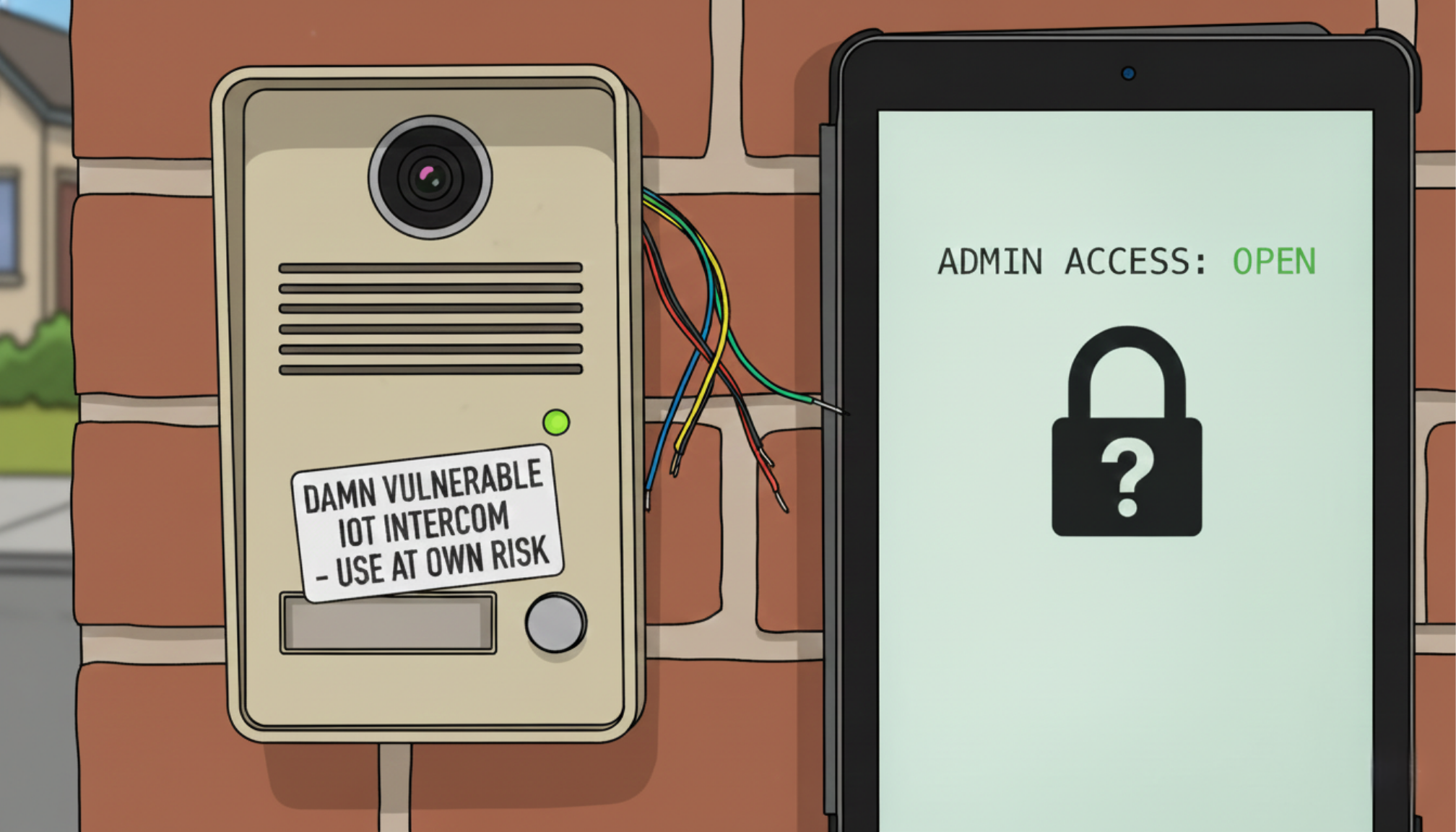
What happens when you take apart a “smart” intercom and discover it’s not so smart about security? It all started when a friend asked me to help configure a smart intercom in a small apartment his...

What happens when you take apart a “smart” intercom and discover it’s not so smart about security? It all started when a friend asked me to help configure a smart intercom in a small apartment his...

This article continues the technical overview of the red-team implant, moving from design goals and baseline configuration to how the device blends into corporate networks without adding endpoints....

In black-box red team operations, physical access can be a legitimate option for initial compromise. During one of these engagements, the plan was simple in concept: clone an employee badge, bypass...